All instant messengers guarantee users the secret of correspondence. But this does not apply to requests from authorized bodies - if necessary, authorities will receive any information about the user, including messages, a list of contacts and a phone number. If such information is available to authorized bodies, it may also become available to attackers. And as always, business is at risk.
In this case study, we will describe how we created the world's first instant messenger for correspondence, which allows the user to communicate without scanning the phone book and the list of contacts.
Prehistory
The customer is a private individual, an individual entrepreneur. By the nature of his work, he communicates with businessmen, politicians, bankers. To communicate, discuss transactions and transfer information, he has to use instant messengers.
All existing instant messengers are linked to the phone book, phone number, and personal data. In the case of hacking, in addition to this information, attackers can get information about transactions, banking, and personal data. People who have to share confidential information need a secure messenger to do it.
The Task
The task was to create an instant messenger without user identification for iOS and Android.
The client’s wishes were as follows:
- The design of the application should be associated with privacy — everything should look encrypted.
- Log in to the chat should be done in several ways, they should all be simple and clear.
- Correspondence should be deleted as quickly as possible.
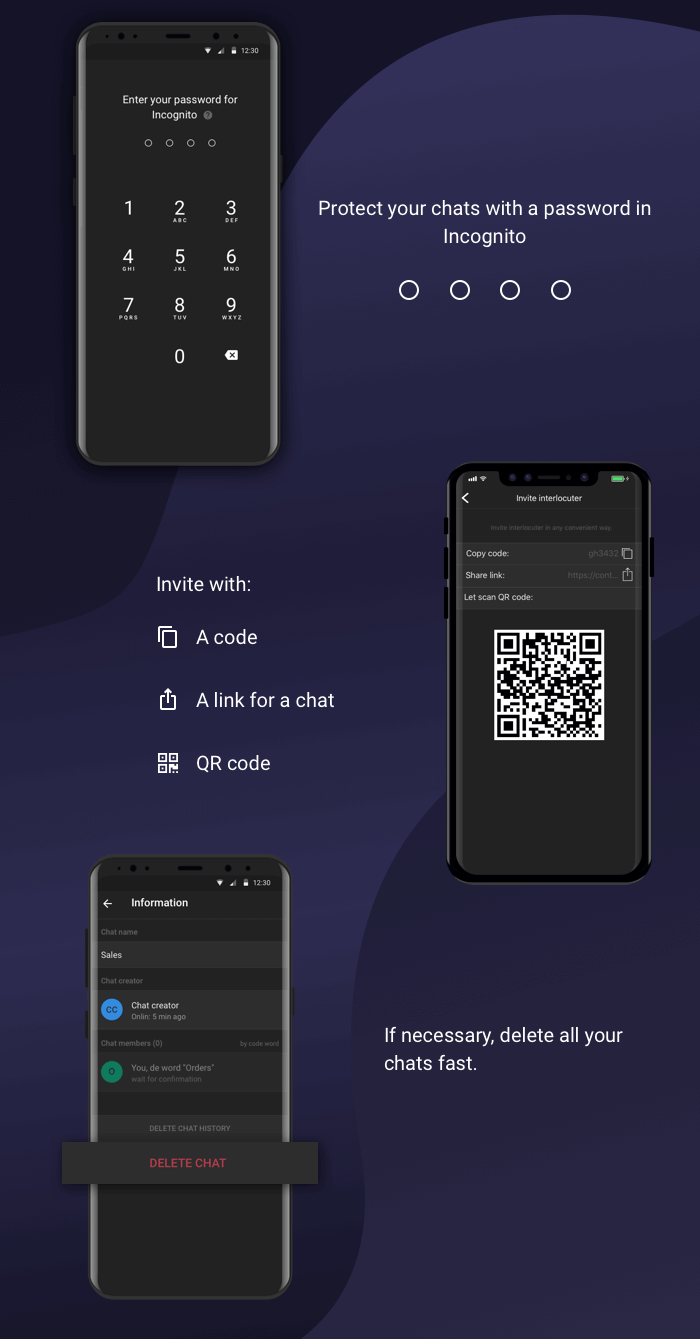
- It should also be possible to set a password for the application so that no one except the owner of the smartphone can get access.
Functional Features
- The application does not require registration. To start using the messenger, you do not need to specify any data, even the name. The application does not have access to contacts and other personal data.
- If someone made a screenshot, the second participant of the conversation receives a notification about it.
- There are no names in the chat.
- You can connect to the chat in several ways.
- After the chat has been deleted, the application does not save any backup copies. There are no archives and correspondence stories.
- You can set a password to log into the application.
- All correspondence is securely protected with a pass-through encryption key. Messages are encrypted according to the most complicated algorithm, where the user comes up with an encryption key.
The Solution
To create an application with such functional features, several tasks had to be solved. We needed to:
- Develop an appropriate design that would emphasize the privacy of the messenger and respond to the wishes of the customer.
- Choose a type of encryption and ensure 100% privacy.
- Transfer all ideas to the program code. At the same time, we needed to ensure the reliability and high speed of the application, as well as its ability to withstand high loads.
To solve these problems, we used a stack of modern technologies.
Design
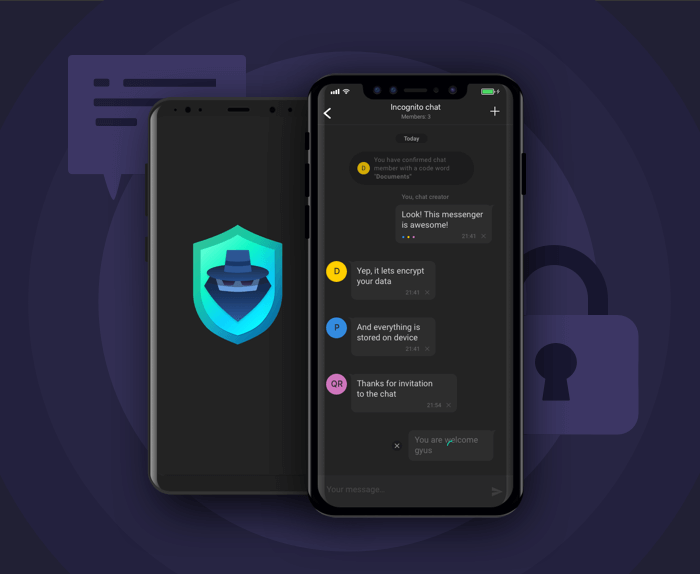
At the first stage, we developed two design concepts: light and dark. We decided to approve the dark since such a design is associated with privacy by the user. For the icon, we also took the image familiar to users - somebody in a hat. We have completed the image of a man in a hat with the help of bright colors. The clickable elements should not merge with the main dark color of the application, therefore, bright, moderately contrasting colors were chosen for them.
Emphasis on Privacy
One of the tasks was to identify participants in the chat without reference to personal data, by which they could be identified. We solved the problem using a code word. Chat participants agree on it in advance outside the application or use a phrase that is immediately associated with the participant in the future dialogue.
In addition to the code word in the chat, the user can configure his additional unique encryption key. After the key is created, the user sees the animation. This enhances the visual effect.
We developed an alert on iOS that another member of the chat made a screenshot of the conversation. In the version for Android, the user can completely disable the ability to take screenshots in the application.
If necessary, all correspondence can be deleted with one click. The application supports the ability to login with a password.
How It All Works from the Inside
Privacy
A distinctive feature of the project is that the user is impersonal, there is no identifier that would hint at the person’s identity. To create a chat, offline users must agree on a code word.
The mechanism is as follows: User A creates a chat, gives it a name and invites users B and C to the chat. Users B and C can enter the chat in three ways:
follow the link
manually enter the code word,
use QR code.
The number of users in one chat is not limited.
Encryption
A cryptographic key is needed to encrypt and decrypt messages. Suppose we exchange secret messages via courier. If the message is not encrypted, the courier can read it. The correspondence must be encrypted, and before that, it is necessary to transfer the secret key to the second subscriber. You can’t just send it, because the courier can decrypt the message. To solve the problem with the exchange of secret keys, we used the Diffie-Hellman algorithm.
In this algorithm, data transfer is based on the principle of end-2-end encryption. It is the most secure protocol in which the encryption and decryption of messages occur without server participation. The server is only a tool to transfer already encrypted messages.
The average processing time for a single message is measured in milliseconds and tends to zero. The server stores only encrypted messages that are not delivered to the addressee (for example, when there is no Internet connection) and automatically deletes them after 7 days if the recipient has not appeared on the network. Only the recipient can decrypt information using the private key. Thus, no trace is left on the servers.
Architecture, Technology Stack
For the development of the back-end, we chose the NodeJS platform. In our opinion, this platform is best suited for chats using sockets. The platform scales easily and quickly. The box solution contains support for 10 thousand connections on one node. The number of connections can be increased to 100 thousand. To do this, it is necessary just to change the settings.
For quick work with chat data and convenient data transfer, we need a NoSQL database (storing the encrypted data until delivery to the recipient). Most companies use MongoDB for this purpose. But for our purpose, this solution was not suitable - there are a number of problems with cleaning files after deleting records, as well as with scaling in MongoDB.
Therefore, we chose RethinkDB as the database. This database has no such problems and there is a convenient syntax for working with an RQL (Resource Query Language) sample.
Android
The Android app is written in Kotlin and follows the latest Google recommendations. We created the messenger based on the MvVM architecture design pattern using the Android Architecture Components. This template allows creating a flexible architecture. Therefore, in the future, we can easily extend the functionality of the application.
iOS
To create an application for iOS, we used our Scaffold-based on the MvVM design pattern. In the future, it will be possible to expand the functionality of the application.
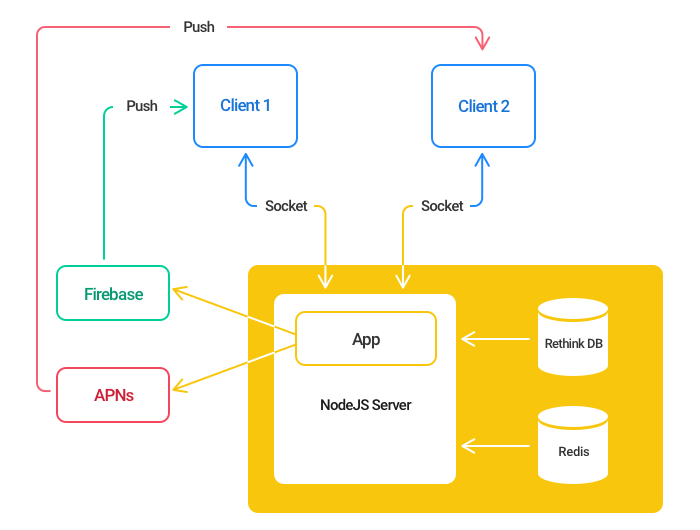
The application Incognito Private Messenger provides 100% privacy.
This is the main advantage of the project in comparison with analogs. User correspondence is stored only on clients. The server stores only the binding of devices to the chat and notifications. There are no keys or any other information that would compromise the encryption algorithm.
The Unique Solution
Standard user verification in the messenger is impossible since there are no phone numbers. Therefore, we have developed an algorithm for checking each client that connects to the chat:
At the time of adding a new chat member, users change key pairs and, when decrypted, authenticate each other.
If everything is alright, the chat administrator approves the entry of a new member.The original keys are stored in a protected area of the device’s memory. And to encrypt the codes, the Diffie - Hellman protocol is used, therefore it is impossible to forge them.
Conclusion
Incognito Private Messenger is unique in its kind.
Furthermore, by increasing the need and number of users, we will expand the functionality of the application. We have provided all the possibilities for this.
In addition, we are currently working on the localization of the messenger and soon it will be available for download in English.